For years, the world of cryptocurrency has been synonymous with cutting-edge digital security and the constant threat of sophisticated cyberattacks. The community has honed its skills in protecting its assets from malware, fraudsters, and cybercriminals. But what if the biggest threat to your cryptocurrency is not lurking in the digital shadows, but right outside your door, wielding something as primitive as a “wrench”?
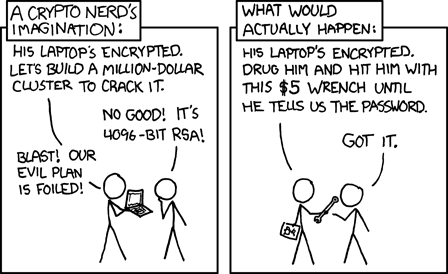
Our paper, “Investigating Wrench Attacks: Physical Attacks Targeting Cryptocurrency Users,” published in the Advances in Financial Technology Conference (AFT 2024), shatters the illusion that cryptocurrency crime is purely an online phenomenon. It exposes a deeply unsettling reality: physical “wrench attacks”, crimes where perpetrators use force or the threat of force to steal cryptocurrencies. These attacks are violent, underreported and alarmingly effective. In recent months, the cryptocurrency ecosystem has been shaken by a surge of serious and violent wrench attacks, including kidnappings and murders. An example is the recent kidnapping of David Ballad, the co-founder of Ledger, the famous cryptocurrency hardware wallet company. Wrench attacks have existed since Bitcoin’s early days, even affecting prominent figures in the space like Hal Finney.
Beyond the Keyboard: What is a $5 Wrench Attack?
The term “wrench attack” originated from a popular XKCD webcomic, depicting a scenario where a physical threat (a $5 wrench) is used to extract information from a victim’s computer, bypassing complicated digital security without the need for technical efforts. In the context of cryptocurrency, these attacks are precisely that: old-school physical assaults or threats targeting cryptocurrency owners to illegally seize their assets or the means to access them. In our paper, we propose the first formal legal definition of the attack, in addition to its crime elements as per criminal law norms, to help identify the precise scope and measurement of the attack.
What makes these attacks so distinct and perilous compared to any other cryptocurrency crime?
- Physical Crime Scene: Unlike cyberattacks, the crime occurs in the real world, hence directly endangering users’ physical safety.
- Primitive Crime Methods: Attackers forgo technical skills, reverting to conventional crime methods like violence, robbery, and blackmail.
- Crimes Against Persons AND Property: The targets are not just the cryptocurrencies (property), but the users themselves.
- Bypassing Digital Security: No amount of cybersecurity alone can protect funds when a victim faces a direct physical threat.
- Universal Vulnerability: Everyone is a potential victim, regardless of their technical/cryptocurrency experience or security awareness. Even seasoned users and early adopters are not immune.
The Hidden Anatomy of a Wrench Attack: Who, How, Why?
To gain a deep understanding of this emerging threat, we conducted the first and only comprehensive study of wrench attacks. We leveraged a unique interdisciplinary approach involving criminal law, criminology, and computer security. Collecting data for such a serious and sensitive topic was extremely difficult. To this end, we conducted 10 interviews with victims and experts, analyzed 146 news articles reporting crimes, and 37 online forums. We used data triangulation, combining the results of these three datasets to overcome biases, and then applied crime script analysis. Crime script analysis is a popular methodology in criminology whereby crimes are dissected into steps/stages, showing every action offenders take along the way.
Who?
Our findings reveal a disturbing diversity in modus operandi and perpetrators. For instance, we find a diverse range of attackers ranging from organized crime groups, to friends/family, domestic partners, and even some corrupt law enforcement agents.
How?
We find wrench attacks occurring in various ways, including burglaries, kidnappings, murder, and blackmail. Alarmingly, we also identify wrench attacks taking the form of domestic abuse, which we note as a new form: “cryptocurrency-facilitated domestic economic abuse.”
As for victim selection, many are chosen non-randomly. This is either due to the person being a public figure, presumed to be an owner (e.g. an engineer in a cryptocurrency service providing company, or a specialist academic), or identified as an owner when transacting in person, etc. Sometimes, offenders are simply opportunistic, for example, a cryptocurrency user being attacked after bragging loudly about their returns.
Why?
Often, it is simply easier for criminals to obtain cryptocurrencies through physical force than through complex cyberattacks. Additionally, the absence of transaction limits in many cryptocurrency service providers, in contrast to traditional banking, can assist in cashing out funds without limits.
Why the Silence? The Alarming Issue of Underreporting
Despite their severity, wrench attacks are underreported. Victims often refrain from contacting law enforcement due to privacy concerns, fears of revictimization, a lack of confidence in police understanding of cryptocurrency crimes, or scepticism about successful outcomes. This creates a “dark figure” of crime, making it difficult to gauge the true scale of the problem.
What can be done to protect against wrench attacks?
In the paper, we offer actionable recommendations for users, the industry, and regulators to combat this evolving threat. Below are some of these recommendations for users:
- Keep a Low Profile: Avoid publicly disclosing your cryptocurrency holdings or discussing specific amounts. Be cautious even in online forums, as pseudonyms can sometimes be linked.
- Strategic Fund Management: Diversify your holdings across different storage methods (hot and cold wallets) and even geographical locations to avoid a single point of failure.
- Combine Digital and Physical Safety: In addition to the myriad of advice provided online about cybersecurity measures, physical security is also key. Cultivate situational awareness, avoid revealing your travel plans or personal information online or in front of untrusted people, and be diligent when attending in-person cryptocurrency gatherings.
- In-Person Peer-to-Peer Transaction Precautions: If engaging in peer-to-peer (P2P) in-person exchanges, thoroughly vet your counterparty, meet in crowded public places, have an escape plan, and start with smaller transactions to build trust. In our paper, 25% of attacks occurred during P2P operations.
A Call to Action
Since the paper’s publication last year, wrench attacks have unfortunately been increasing rapidly across the globe. Whilst we acknowledge the tremendous efforts and cooperation of certain law enforcement agencies and news outlets in spreading awareness through our recommendations, we urgently call on industry actors and regulators to intervene to minimize the occurrence and the aftermath of these dangerous attacks.
Acknowledgements
Thanks to Marie Vasek, Alice Hutchings, Gilberto Atondo Siu, and the Cambridge Cybercrime Centre