I was at the EuroUSEC ’17 workshop in Paris at the end of April. Our own Angela Sasse was also there to deliver the keynote talk, and Ruba Abu-Salma presented our paper “The Security Blanket of the Chat World: An Analytic Evaluation and a User Study of Telegram” (which was based on research by undergraduate students studying UCL’s COMP3096 “Research Group Project” module). I presented secondary analysis, conducted with Ingolf Becker and Angela Sasse, of a survey deployed at a large partner organisation. This analysis builds on research we presented at the Symposium on Usable Privacy and Security (SOUPS) in 2016. Based on survey responses and voluntary free-text comments, we saw potential for employees to inform policy from the ‘ground up’, in contradiction to the current trend for identifying security champions as local representatives of pre-determined policy.
Top-down security policies
Organisational policies are intended to promote a unified approach to security, one that all the organisation’s employees are expected to follow. If security procedures and mechanisms are unusable, policies risk being seen as impossible to follow, or may be sidelined if they lack clear relevance to business goals. This can result in deliberate or unwitting non-compliance, and workarounds to prescribed procedures.
Organisations may promote security champions, as local representatives to promote policy in their part of the organisation. However, these security champions can be effective only if policy is workable. Encouraging ‘top down’ policy compliance assumes that policy is correct, complete, and appropriate. It also assumes that policy applies to everyone equally and that employees have no role to play in shaping effective policy. Our analysis explores the potential for employees to inform effective policies, in particular whether it was possible to (i) identify local pockets of security expertise, and (ii) target engagement with employees that involves them in the creation of workable security solutions.
Identifying security champions ‘from the ground up’
| Level | Attitude | Approach |
| 1 | Uninfluenced | Security behaviour is driven by personal knowledge. |
| 2 | Technically Controlled | Technical controls enforce compliance with policy. |
| 3 | Ad-hoc Knowledge and Application | Shallow understanding of policy. Knowledge absorbed from surrounding work environment. |
| 4 | Policy Compliant | Comprehensive knowledge and understanding of policy. Willing policy compliance. Role model for organisation’s security culture. |
| 5 | Active Approach to Security | Actively promote and advance security culture. Intent of policy carried into work activities Leverage well-understood values that support both security and business. |
A scenario-based survey was deployed in the partner company. Scenarios were based upon in-depth interviews with employees that explored security behaviours in the workplace. Each scenario involved a dilemma, where fixed options described different responses and included an element of non-compliance or an implicit cost. Participant choices indicate their Behaviour Type (above) and Attitude Level (below), which we recorded across groups of employees to characterise the security culture of the organisation and in four specific divisions. Both interviews and surveys represent a cross-section of divisions, locations, and age groups. We collected 608 survey responses; crucially, the survey allowed participants to comment on the scenarios and the available options – we also looked at 267 additional free-text comments that were provided.
| Behaviour-Type | Description |
| Individualists | Rely on self for solutions |
| Egalitarians | Rely on social or group solutions |
| Hierarchists | Rely on existing systems or technologies |
| Fatalists | Take a ‘naive’ approach, that their actions are not significant in creating outcomes |
Most participants provided responses that indicated a high attitude level. The table below illustrates response rates for optional comments, where response rates generally increase with security attitude level for all behaviour types. That Hierarchists and Fatalists make fewer comments is in keeping with their behaviours — that is, not questioning rules, either because they adhere strictly to the policies or because they consider security to be ‘somebody else’s job’.
| Behaviour type | Level 2 | Level 3 | Level 4 | Level 5 |
| Individualist | 2.01% | 8.72% | 20.81% | 25.50% |
| Egalitarian | 3.33% | 0.00% | 15.00% | 26.67% |
| Hierarchist | 0.78% | 1.17% | 8.98% | 20.70% |
| Fatalist | 2.48% | 4.46% | 10.40% | 17.82% |
Behaviours and Attitude to security in the organisation
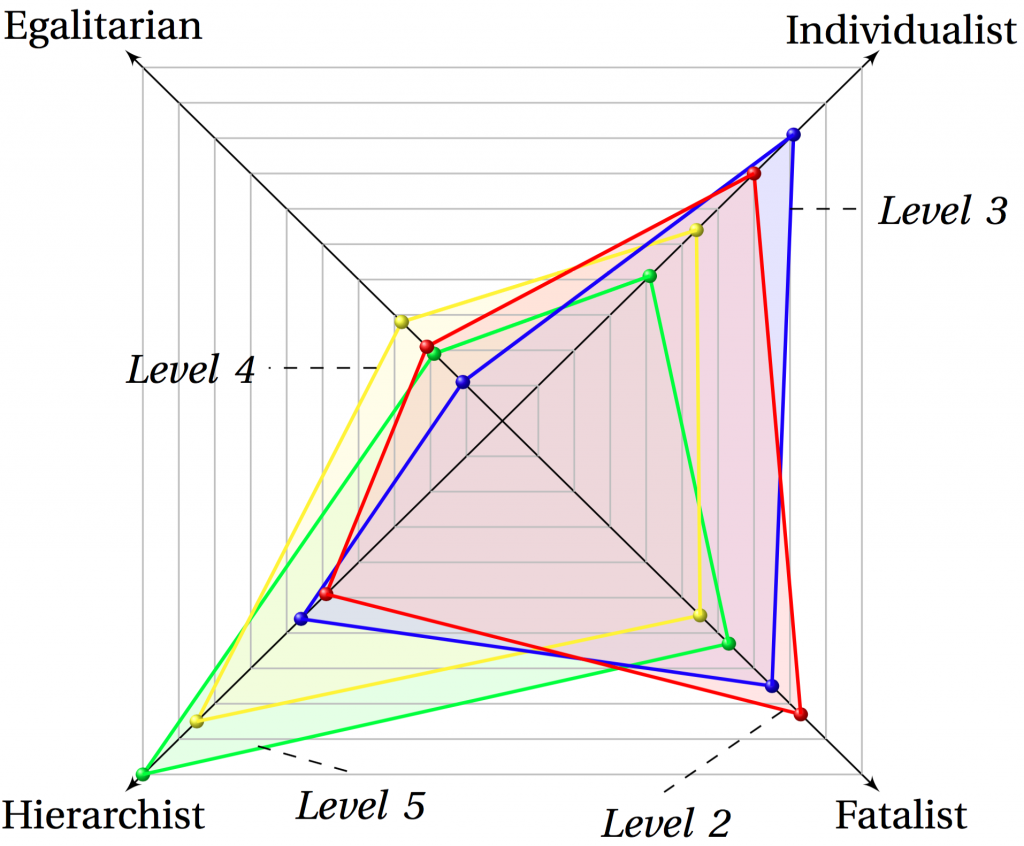
We plotted the survey scores in Kiviat diagrams (as above for the whole organisation). Each diagram has four tetragons plotted, one for each attitude level. The diagonal axes represent the fraction of participants that exhibit each personality type, with the centre of the diagram being 0%. As an example, in the diagram above the blue tetragon represents participants at attitude Level 3 (‘Ad-hoc Knowledge and Application’). Of these, 4.5% (4 employees) exhibit as Egalitarian, 36% (29 employees) as Individualist, 34% (27 employees) as Fatalist and 26% (20 employees) as Hierarchist behaviour types. This distribution is very different to Level 5 attitude types, where 45% (212 employees) of participants belong to the Hierarchist group.
Referring to the Attitude Levels, there is a disparity between Levels 2–3 and Levels 4–5, suggesting not just that distinct approaches to employee engagement would be needed, but that the messaging would have to be crafted to match the relationship that employees have with security and security policy. The limited representation of Egalitarian behaviours would suggest that individuals respond to security challenges in isolation.
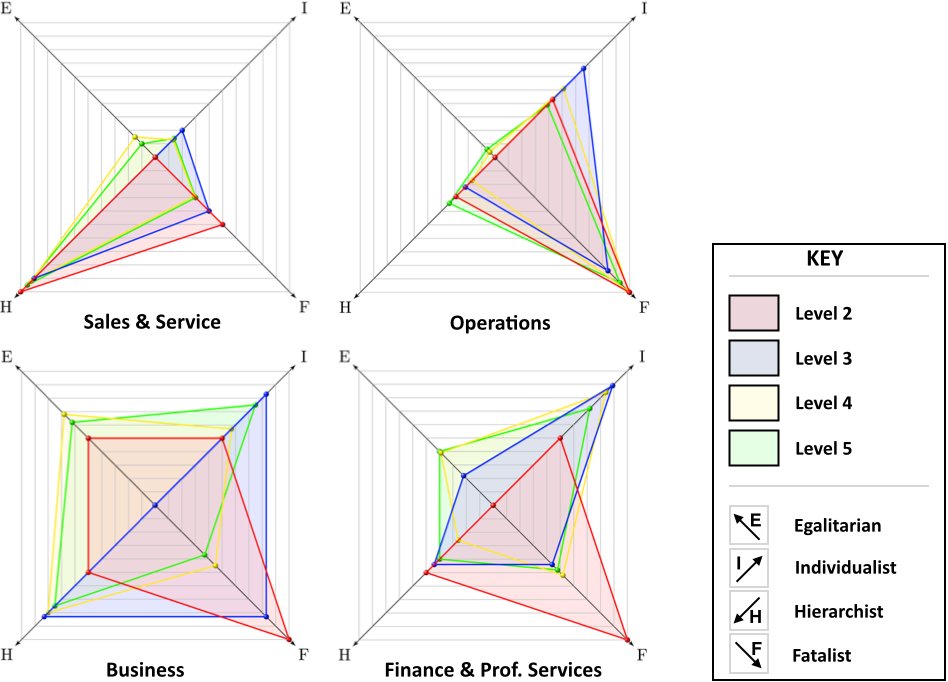
Looking at specific divisions, in the Sales & Service division (above, top-left) approximately 63% (248 employees) of participants are Hierarchists (compared to 40% for the whole organisation. The free-text responses for this group included additional comments regarding a scenario where — due to IT limitations — the scenario’s protagonist is unable to securely send data to a client. As an example:
“The employee is put in a no-win situation. If the business permit flexible working then the only allowable option here is for the data not to be sent.”
In the Operations division (above, top-right), 55% (65 employees) of employees at attitude Level 5 are Fatalists. If Fatalists see their own actions as irrelevant to the preservation of security, it may be that there is a separation from the larger organisation’s security function or that employees perceive security as being addressed by someone else. That these employees are at Level 5 (‘Active Approach’) implies that their security understanding — which may or may not stand alongside policy-compliant security — is superb. One employee voices their opinion when considering the expectation of having to share passwords:
“Assuming he can change the password straight after – that’s not too bad.”
In the Business division (above, bottom-left) there is a more diverse security culture, including an approximately equal mix of Egalitarians, Hierarchists and Individualists. This alone suggests that a ‘one-size-fits-all’ approach to engaging with employees might not reach everyone in the division. The free-text responses from this division were varied, showing security compromise as well as policy enforcement. One participant stands up for the policy, declaring that the actions offered to address the survey question’s dilemma are not sufficient. When faced with the prospect of transferring data over an insecure connection, s/he states:
“Would liked to have seen this option as a choice: [additional option] Report the [connection] problem and sit back until its fixed. Ignoring the fact that the work is crucial.”
This division contains the highest proportion of Egalitarians of all the divisions considered. A typical comment from an Egalitarian person, when encountering an unlocked and unattended workstation, is:
“[I would] send an email from the user of the unlocked machine to the team, offering to buy ice creams for everyone.”
In the Finance & Professional Services division (above, bottom-right), the predominant behaviour type is Individualist: approximately 40% (26 employees) of attitude Levels 3, 4 and 5 display this type. In this division, there is a discrete switch from Fatalist to Individualist from attitude Level 3 (‘Ad-hoc Knowledge and Application’) upwards. It might be that those employees whose jobs are constrained by IT are relying on the organisation to ensure security for all, whereas those with an understanding of policy feel that they own how it is applied.
Our analysis suggests that practitioners and researchers ought to explore the potential for regular, direct, two-way interaction as a means to align security policy with the reality of work activities in an organisation. Awareness initiatives should be targeted, which can include not only surveys, but also workshops, and individual interactions with employees; this effort is necessary to understand relevant risks and workplace motivations towards security. If security doesn’t work for people, it doesn’t work.
Our full paper, Finding Security Champions in Blends of Organisational Culture by Ingolf Becker, Simon Parkin and M. Angela Sasse, is available from the Internet Society.